Reftab can query your LDAP server and add users as loanees into Reftab. Loanees cannot login, they are simply saved into your Reftab account as borrowers of equipment.
Note: LDAP connection to Reftab does not delete loanees it only adds them into Reftab. So for example if a user joins the organization, when they are added to your directory, Reftab can pull that loanee in, but if the user leaves the org, and is removed from your company’s directory, the user will not be removed from Reftab.
NOTE: It is recommended to use a SCIM integration instead of LDAP if possible. Click here to view SCIM setup guide for Azure
Notes on using Self-Signed Certificate
You can setup an LDAP connection to your organizations server via LDAPS with a self-signed certificate. If your LDAP server is exposed via IP address, you can only use self signed certificates.
When configuring in Reftab, paste the certificate in the “TLS Certificate” field and leave TLS key blank. After you provide the other necessary data on the LDAP connection page, click “Test Settings” and Reftab will respond with any relevant connection error notices or success.
How to setup an LDAP connection in Reftab
Reftab users a lookup account user to read your directory. Make sure to use a user with the least amount of read only privileges possible.
Notes on Firewall: We can provide an IP address that you can whitelist in your firewall rules for incoming traffic on port 636 which we recommend for ldaps. Reach out to help@reftab.com for that.
Notes on Sync: Only 1,000 users can be synced.
Log into Reftab. click “Settings” > “JobScheduler” > “NewScheduledJob”
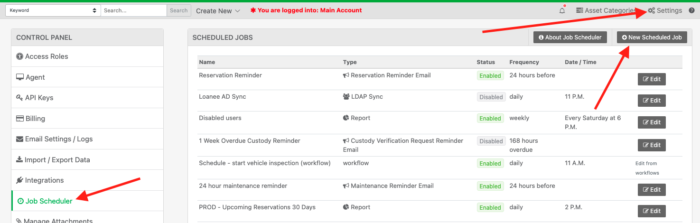
Choose “Sync Loanees via LDAP“
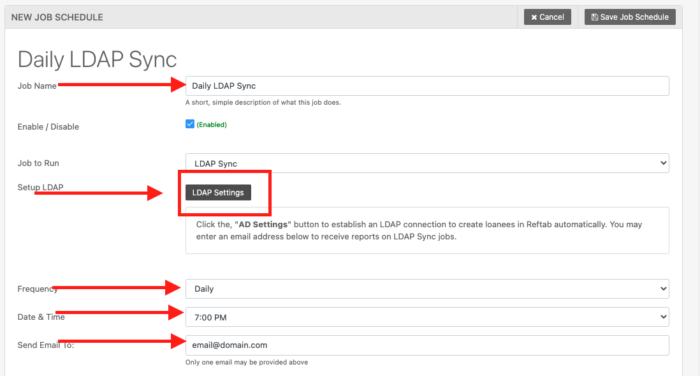
Give the job a name, choose the frequency you’d like to sync and add an email address for alerts and click, “LDAPSettings“
Next, fill out the information according to your directory settings:
NOTE: If your connecting via IP, you can your ldap server’s IP address and use LDAPS:// as the protocol. You will need to provide your TLS Cert and you can leave TLS Key blank.
If you’re using Domain Name and use LDAPS:// as protocol, you’ll need both TLS Cert and TLS Key and the hostname on the cert needs to be publicly resolvable.
Notes on Firewall: We can provide an IP address that you can whitelist in your firewall rules for incoming traffic on port 636 which we recommend for ldaps. Reach out to help@reftab.com for that.
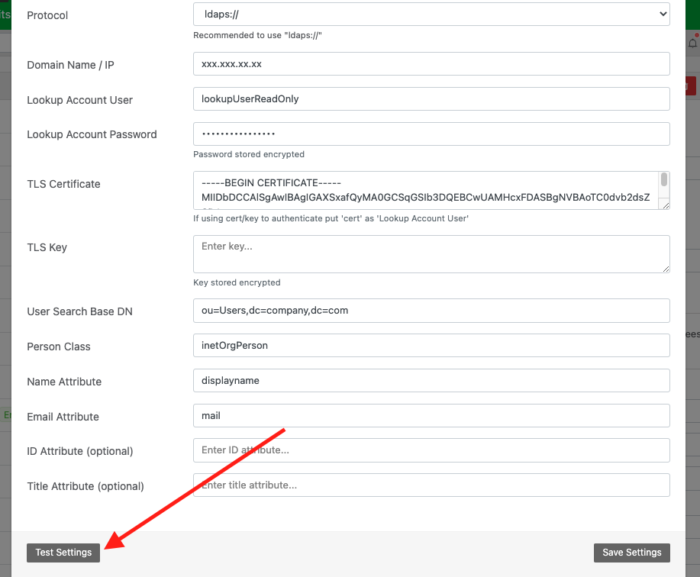
Use the “Test Settings” button to test the connection. Reftab will return any encountered error so that you may use the error to troubleshoot further and make adjustments.