
Integrating with your Azure instance allows Reftab to discover of who has access to your SaaS platforms, and how often they utilize these platforms. This data can flow into Reftab allowing you to have a single-pane-of-glass view into not just your hardware, but software as well.
This guide will cover:
Azure Settings
Permissions Required
Permission Required for O365 Applications
Tracking Software Utilization
Creating a Certificate and Secret
Settings within your Reftab Account
Azure Settings
You’ll need to register Reftab as an application within your Azure account.
Log into your Azure account (https://portal.azure.com), and click, “Enterprise Applications”.
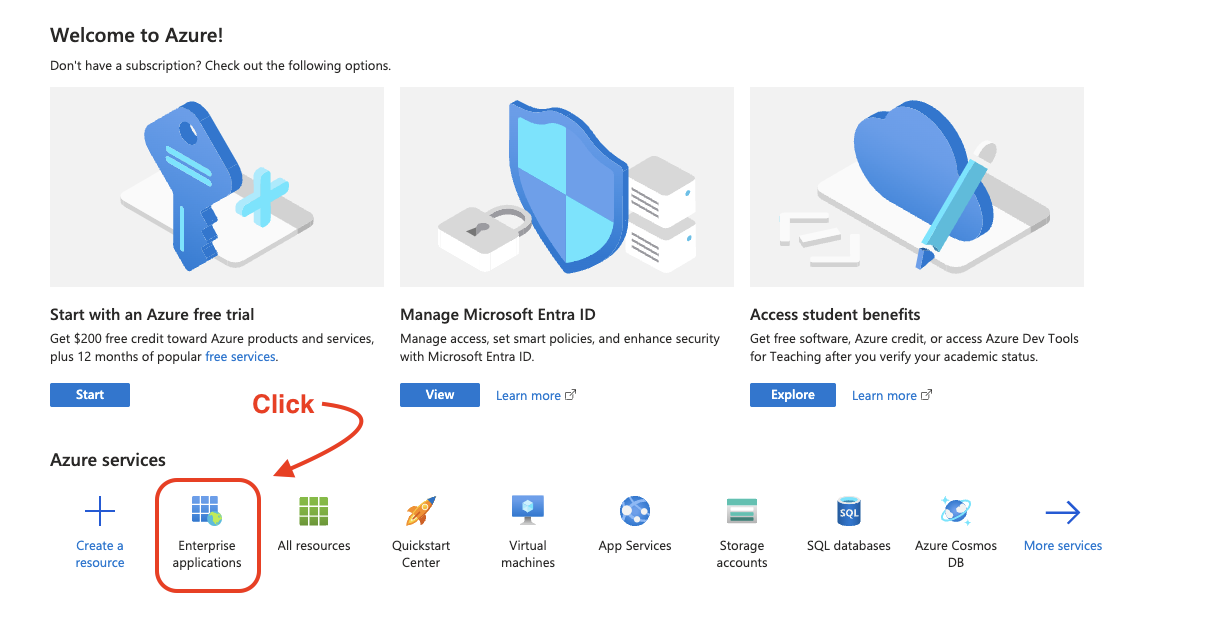
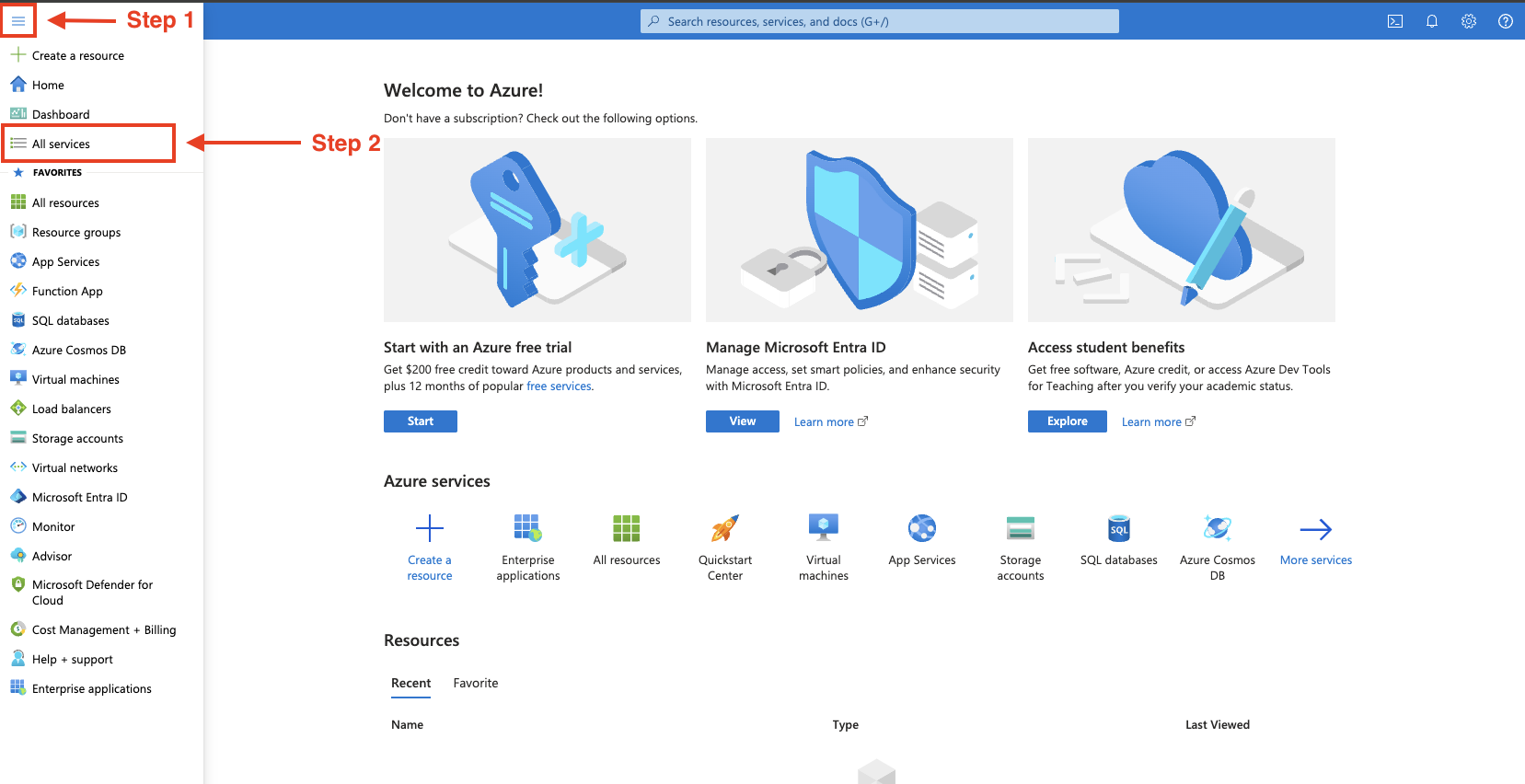
If you do not see “Enterprise Applications”, then you will need to click the menu tree in the top left corner, and then click “All services”. Here you can search for “Enterprise Applications” and star the service so that it can be easily accessed from the landing page.
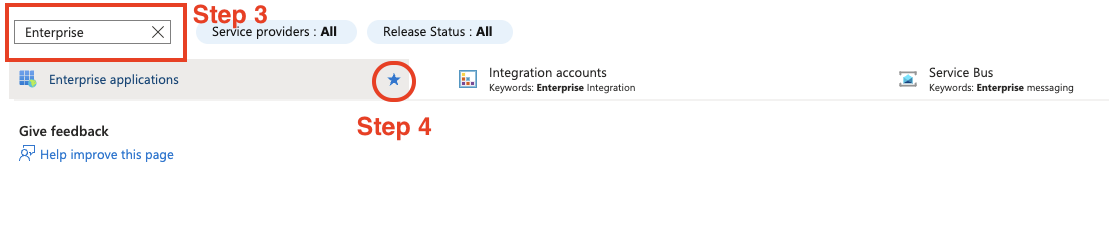
Next, click “New application” > “Create your own application”.
Name the application, “Reftab”. Ensure that “Integrate any other application you don’t find in the gallery (Non-gallery)” is checked. Then press “Create”.


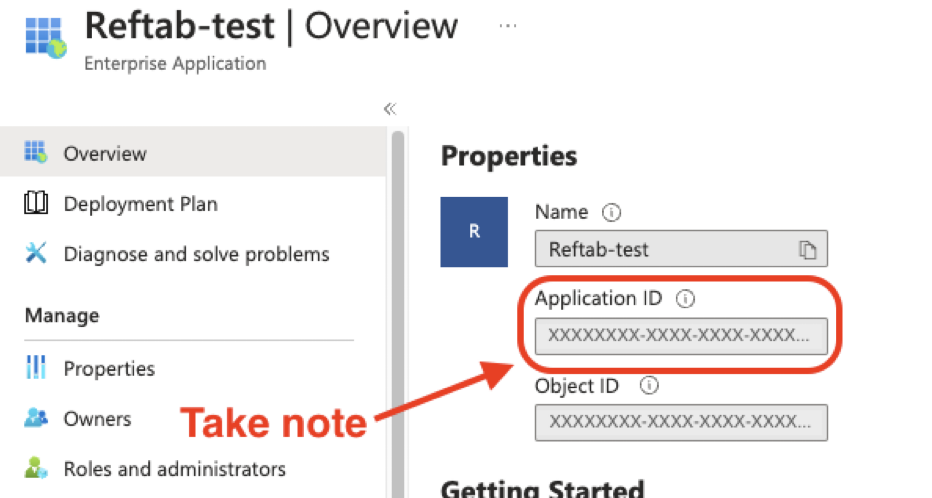
Next, note the “Application ID” under the “Properties”. This will be needed later on.
Grant Permissions
Next the application needs to be granted permissions.
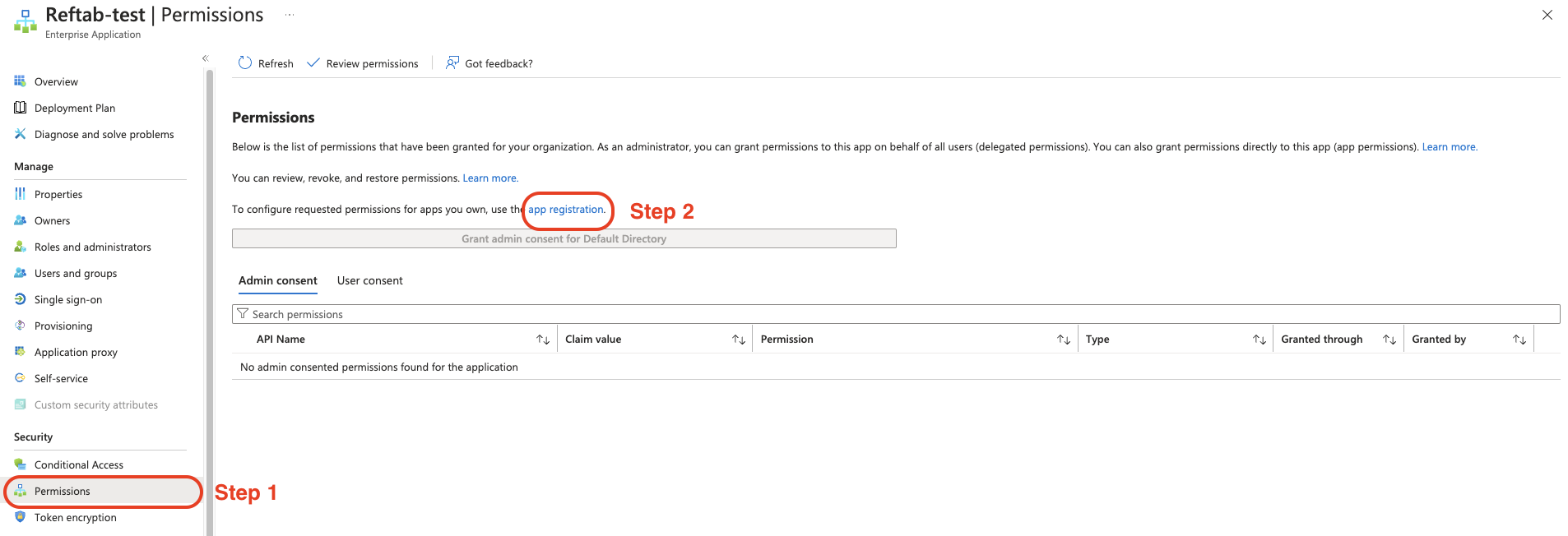
On the left side, click “Permissions“.
Then click, “app registration” > “Add a permission” > “Microsoft Graph”.
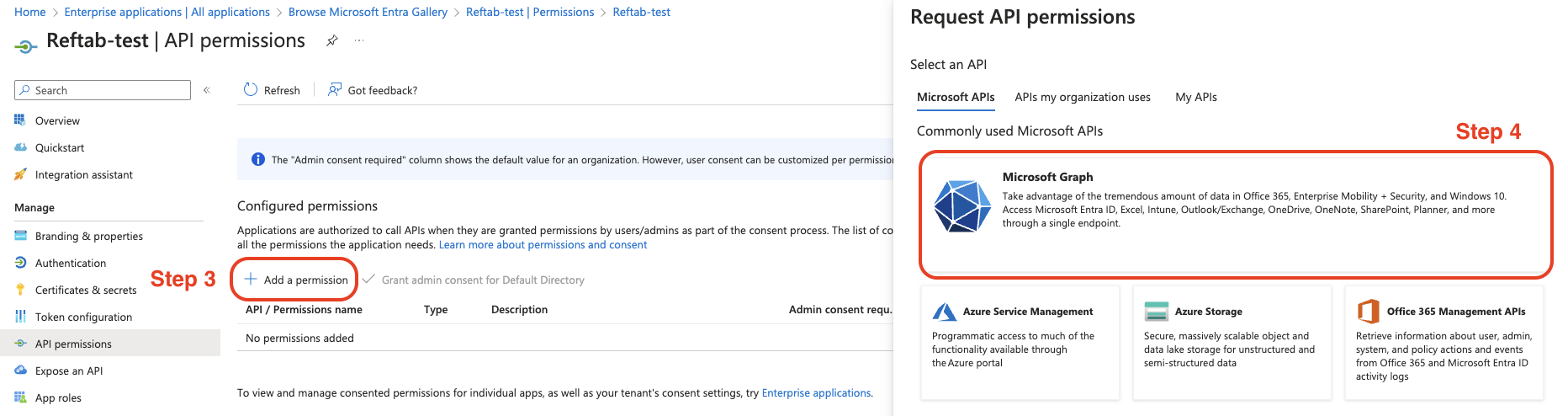
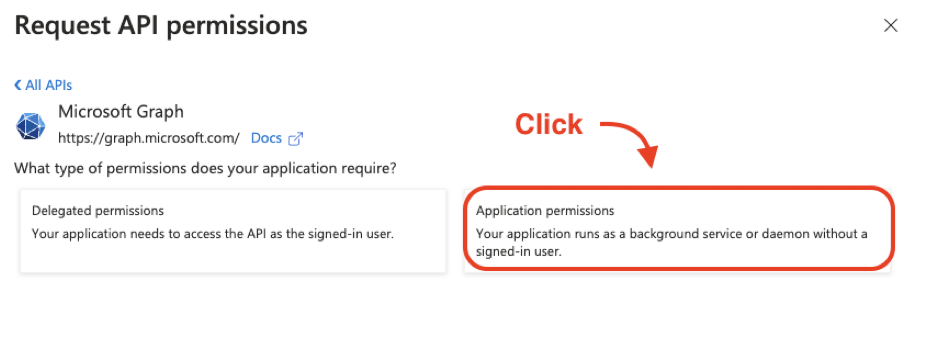
Next click, “Application permissions”.
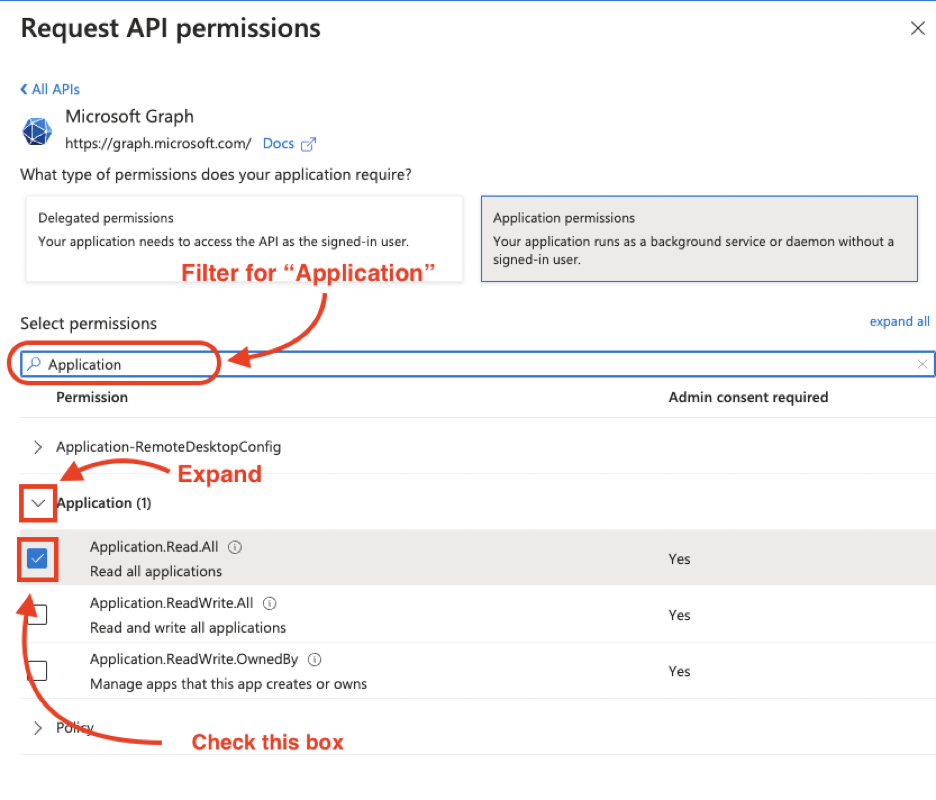
Next, filter by typing in the respective box and search for “Application”, expand the category and check the box, “Application.Read.All”.
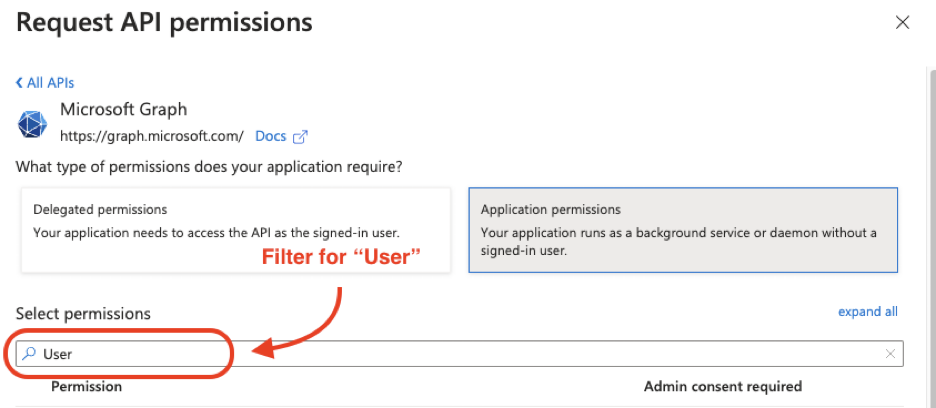
Next, filter for, “User”. Scroll down until you locate the “User” category, expand the category, and check “User.Read.All”.
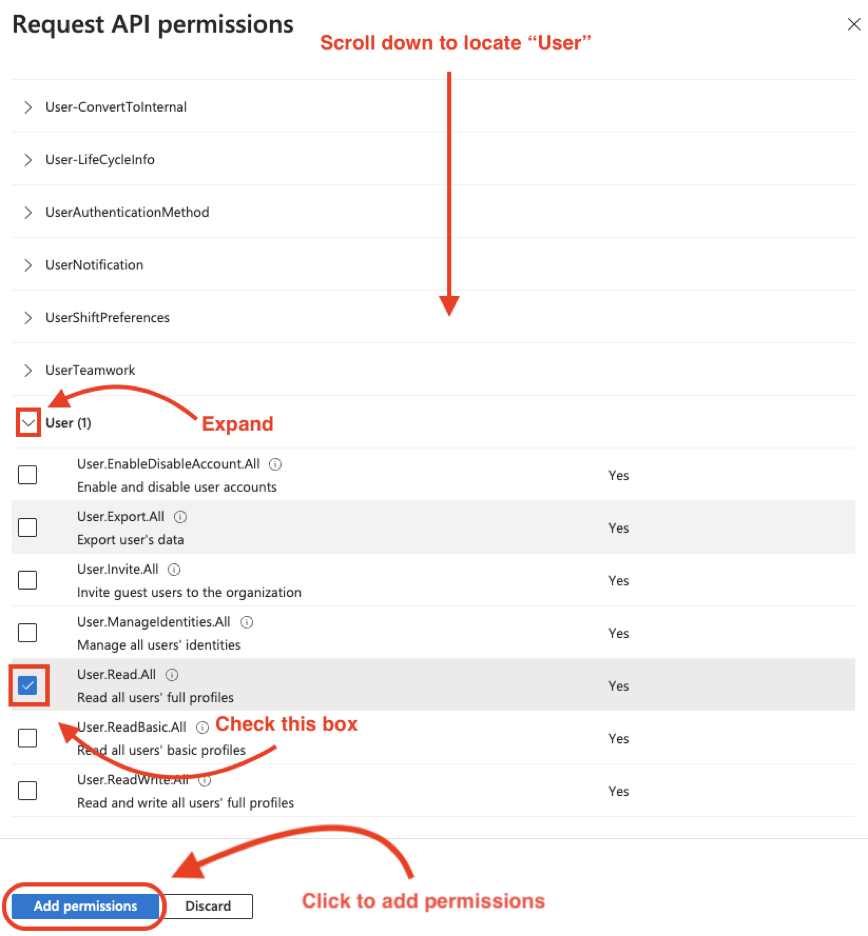
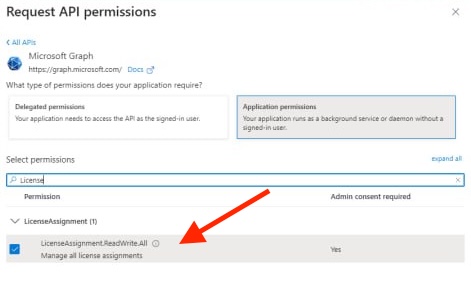
Last, to be able to import Microsoft Office 365 applications, we will filter for “License” and checkmark “LicenseAssignment.ReadWrite.All“. Then click “Add Permission“
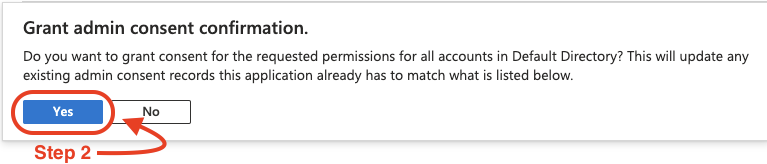
Once permissions have been added, click on “Grant admin consent”, then click “Yes” on the confirmation popup.


Additional Permissions Required to Track Software Utilization
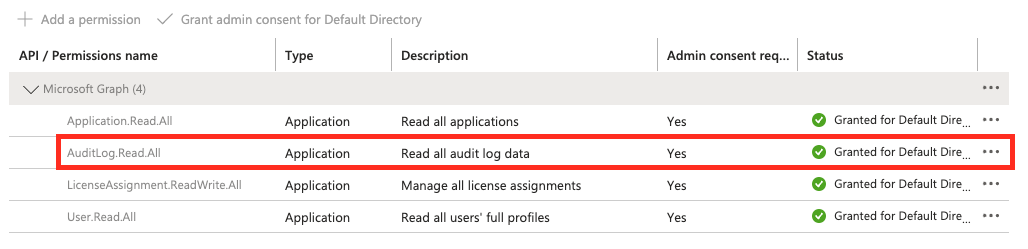
If you want to be able to see within Reftab, the login counts and usage by user, you’ll need to grant the permission “AuditLog.Read.All“.
This screenshot shows what it looks like when this permission is enabled. You’ll see login count per user and a graph of usage over time.
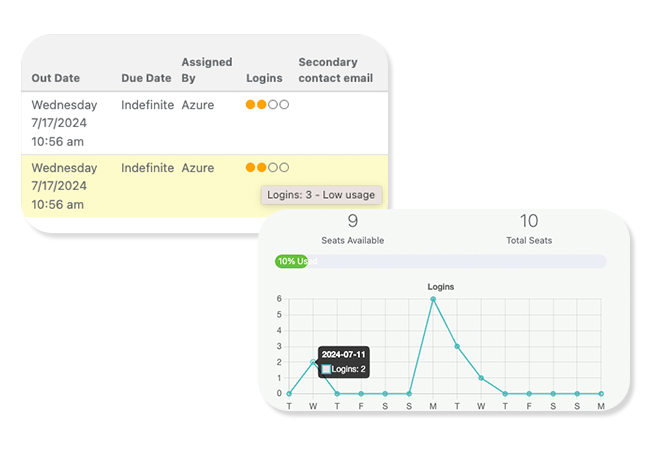
To enable this useful feature, find “AuditLog.Read.All”, as shown below and grant the permission.
This helps ensure you’re getting the most out of your software investments and ultimately reduce seat counts and save money and prevent overspending.
You can learn more about the Okta and Azure SaaS utilization feature here!
Create Certificate and Secret
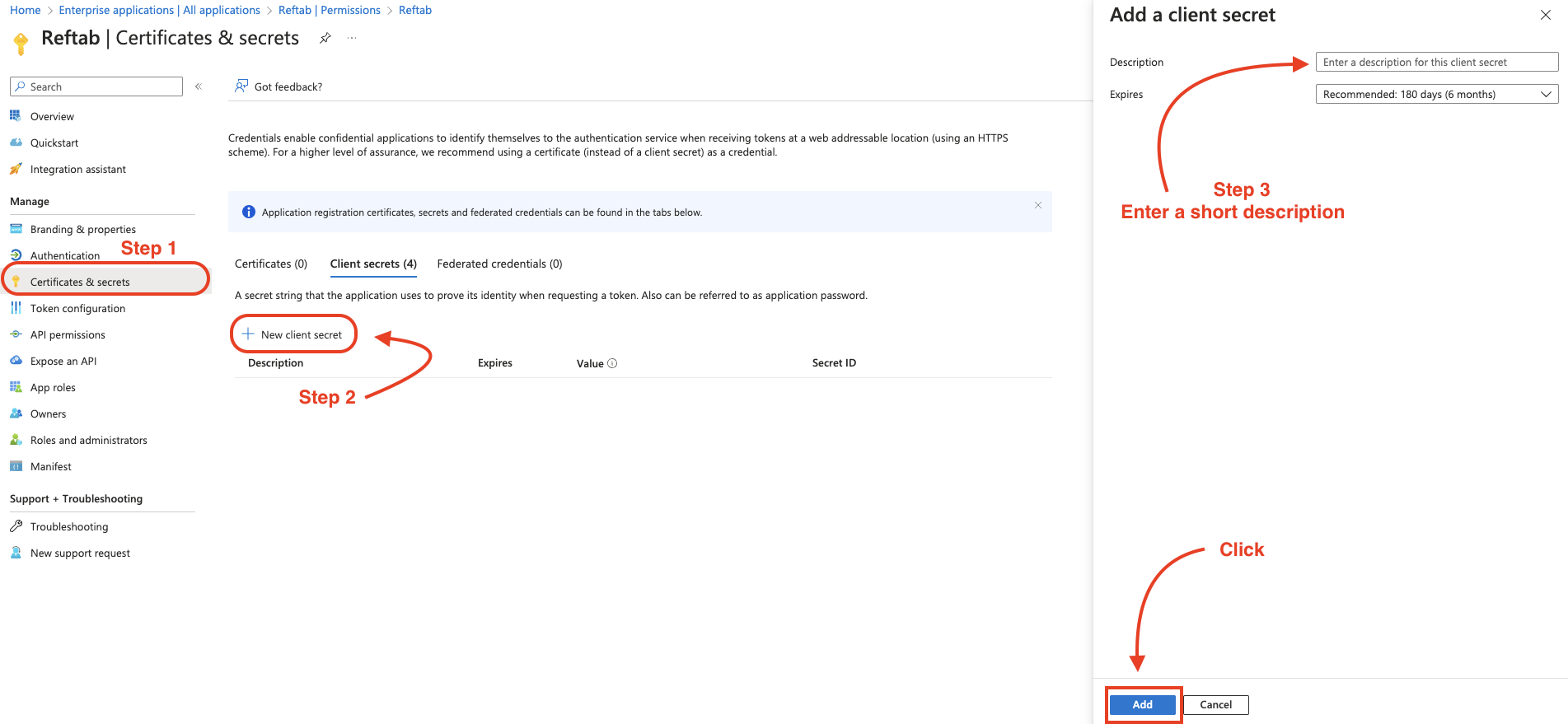
Next, create a new client secret by navigating to “Certificates & secrets” on the left-hand menu, click “New client secret”, then enter a short description, “Reftab”
Set your expiration timeframe, the recommended is 180 days by default. Then click “Add”.
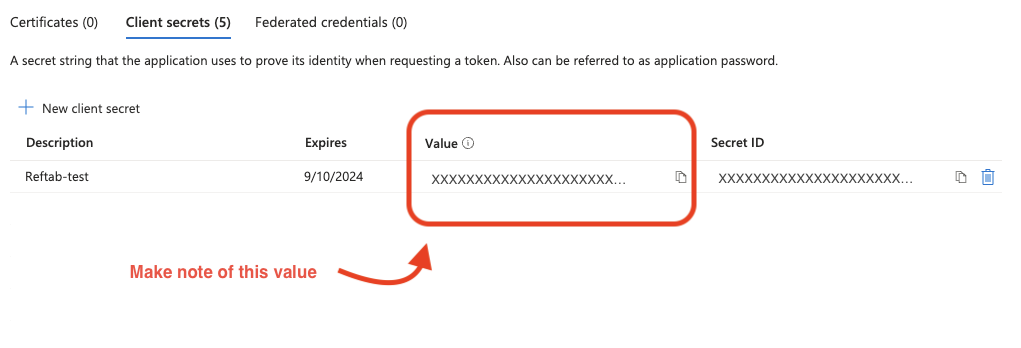
Take note of the string under the “Value” column, as it will be needed later.
**This is the only time that this value will be visible**
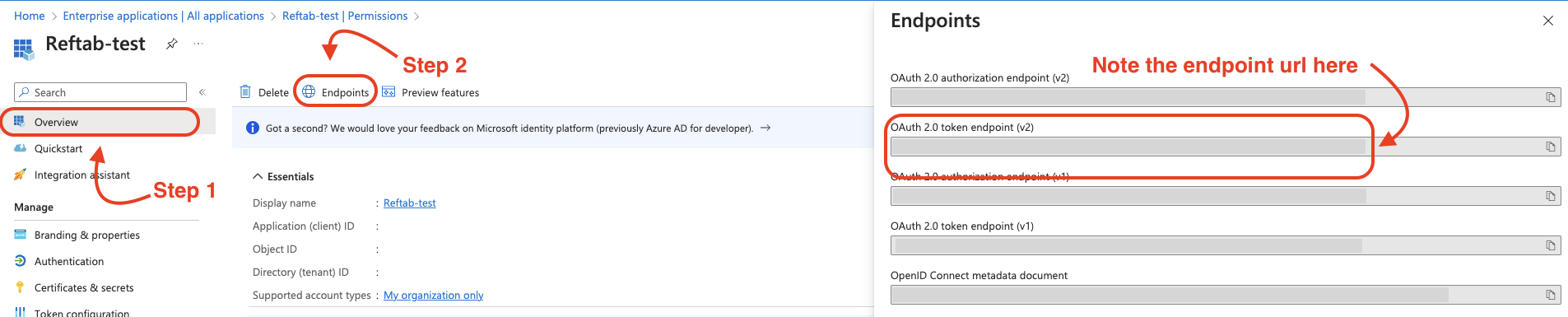
Next, click “Overview” on the same page, and click “Endpoints”.
Copy the OAuth 2.0 Token endpoint (v2), as it will also be needed in the next steps.
Reftab Settings
Now that things are setup on the Azure side, log into your Reftab account: https://www.reftab.com/login
Click “Settings”> “Integrations”, find “Microsoft 365 and Azure SaaS Discovery and click, “Configure”

- Input your endpoint url into the “Azure Oauth2 Token Endpoint” field.
- Input your Application ID into the “Client ID” field.
- Input your client secret value into the “Client Secret” field.
Next click “Save Settings”.
Then click “Refresh Azure Applications”. Your Azure application will now populate.

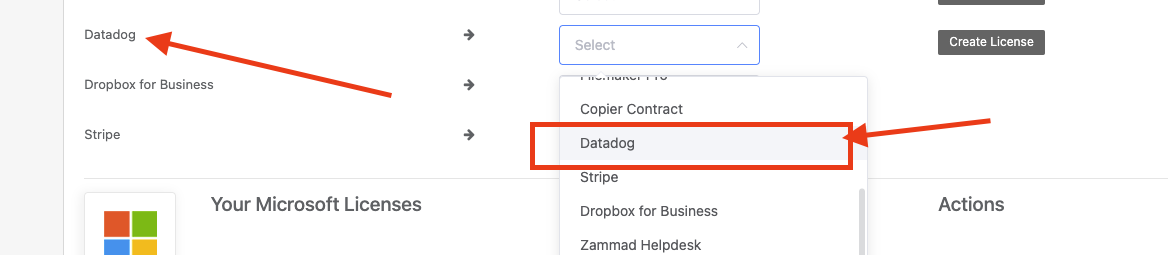
You can now create subsequent applications for each license pulled from Azure by clicking on the “Create License” button next to any you’d like to track within Reftab.

Once you click “Create License” you’ll need to select it in the drop down list.
If you scroll down, you will also see a list of your Microsoft Office 365 applications that can also be created as a license within Reftab for assignment.

After you’ve mapped your applications, click “Save Settings” then click “Cancel“

Then click “Sync Now“

When the sync finishes, click on a license and you’ll see users assigned automatically!

..and there you have it! You have successfully configured Reftab’s Microsoft SaaS Discovery integration!
Note on Sync Frequency: Sync occurs by default every 24 hours.
For questions or any assistance, please email help@reftab.com
