This document provides an overview of configuring Reftab as a SAML application your Azure AD environment to use with Single Sign-On.
To skip to the Just-in-Time Provisioning section, click here
First, sign in to the Azure management portal using your Azure Active Directory administrator account.
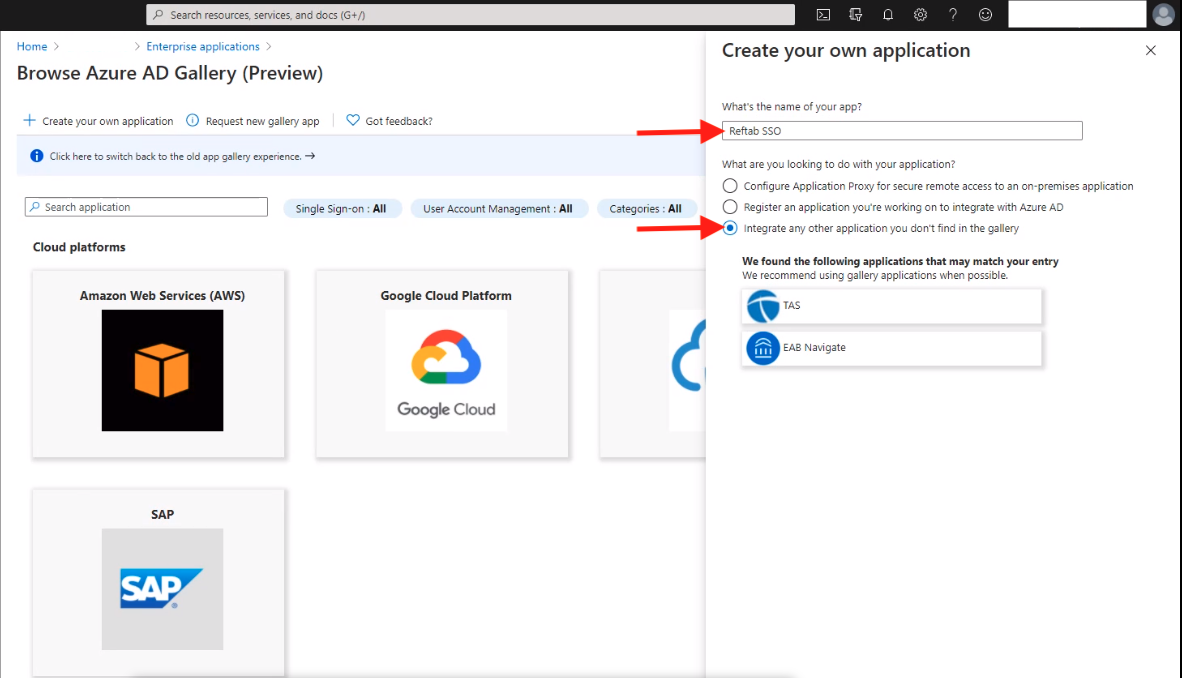
Browse to the Azure Active Directory > [Directory] > Enterprise Applications, and select “Create your own application“
Give the application a name such as “Reftab” and select “Integrate any other application you don’t find in the gallery”. Click “Add”
(Note if you need to search for the application at a later time, you can do so via the “All applications” section.)
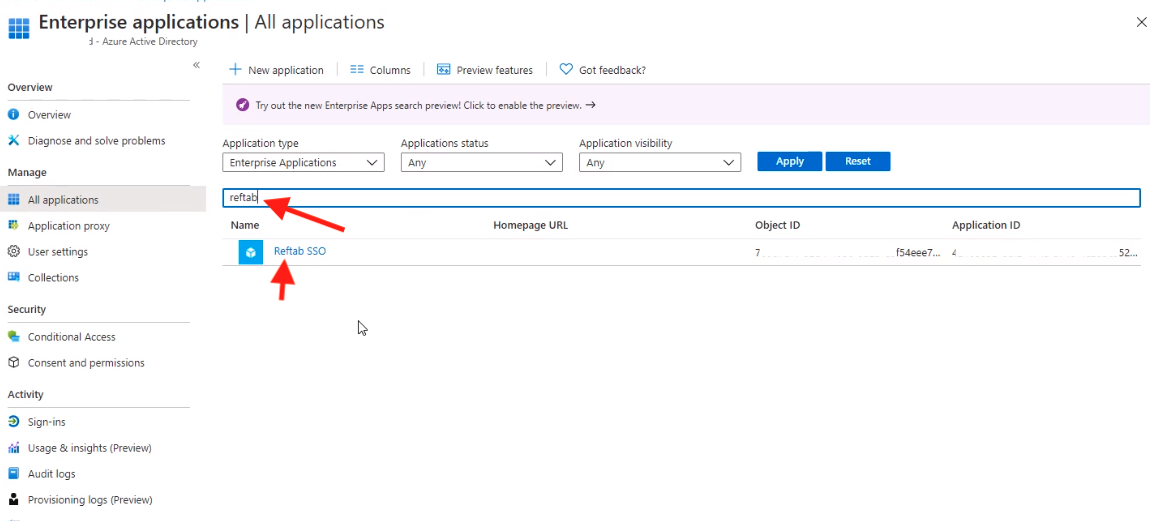
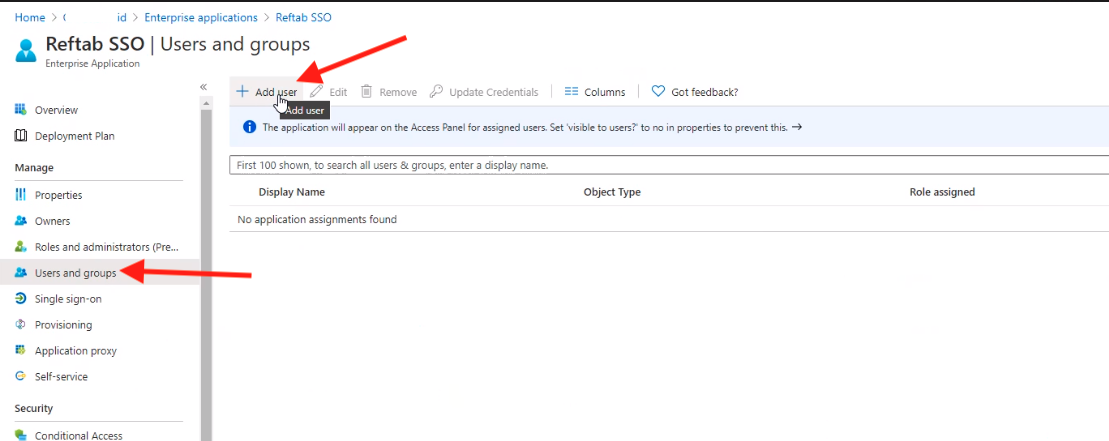
Next, click, “Users and groups” and click “Add User“. Assign at least one user to the application. (Required)
OR – Add an entire group. These are the users and groups that can access this application.
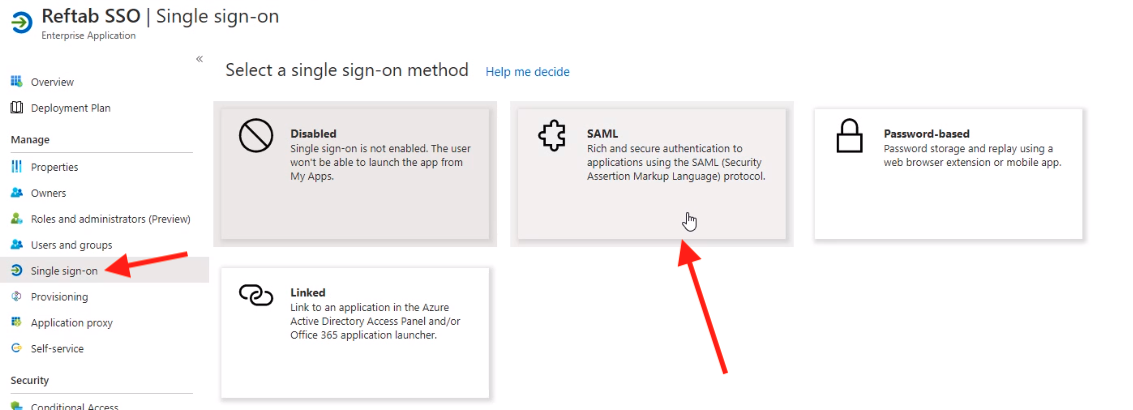
In the “Single Sign-on” section, select “SAML“.
On the next screen, click “Edit” next to Basic SAML Configuration.
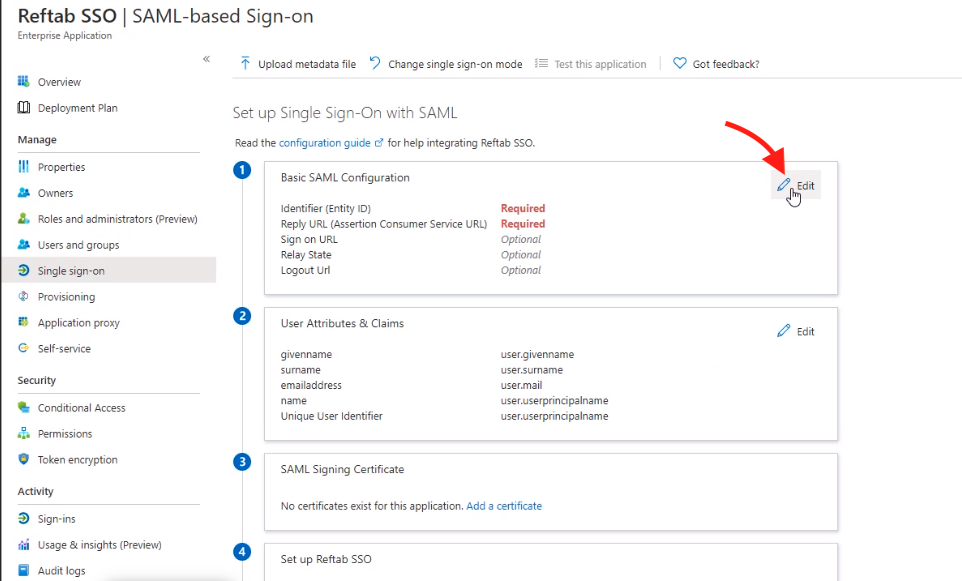
You’ll need to provide the Reftab Identifier and Reply URL:
Identifier: https://www.reftab.com/
Reply URL: https://www.reftab.com/api/sso
Click “Save“.
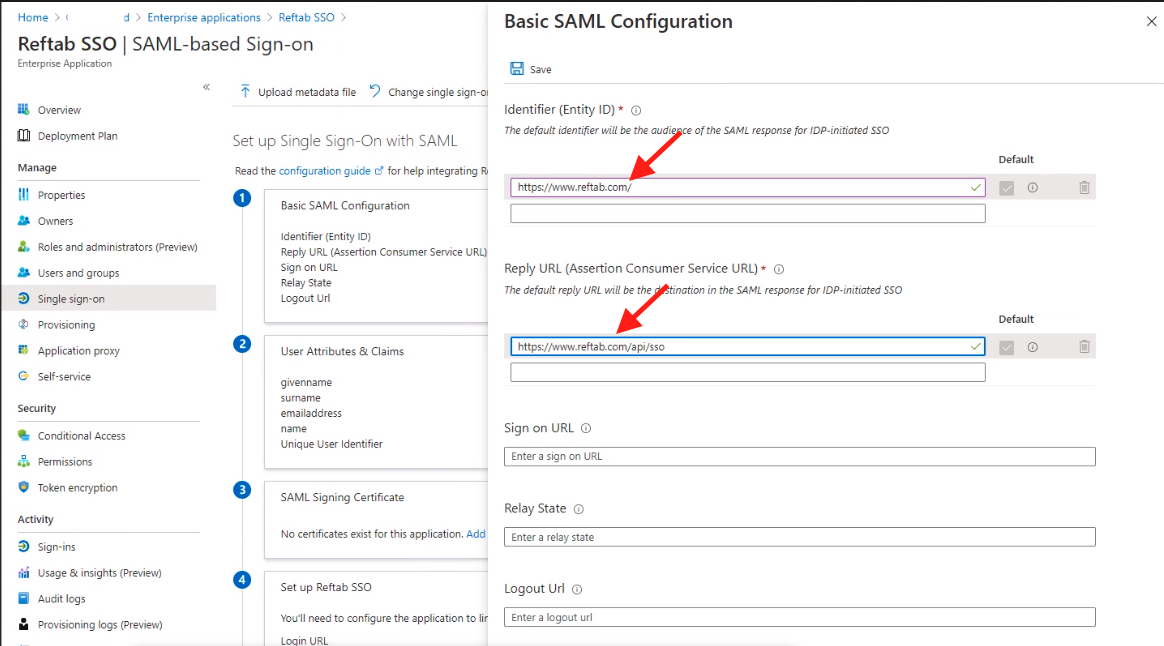
Next, Download the “SAML Signing Certificate” (Base64 format).
Next, copy the App Federation Metadata Url
NOTE: on this screen you can also download the Certificate (Base64) download this if the metadata url doesn’t pull it in on the below steps)
Next, log into Reftab as an administrator. Click “Settings” > “SAML Settings”
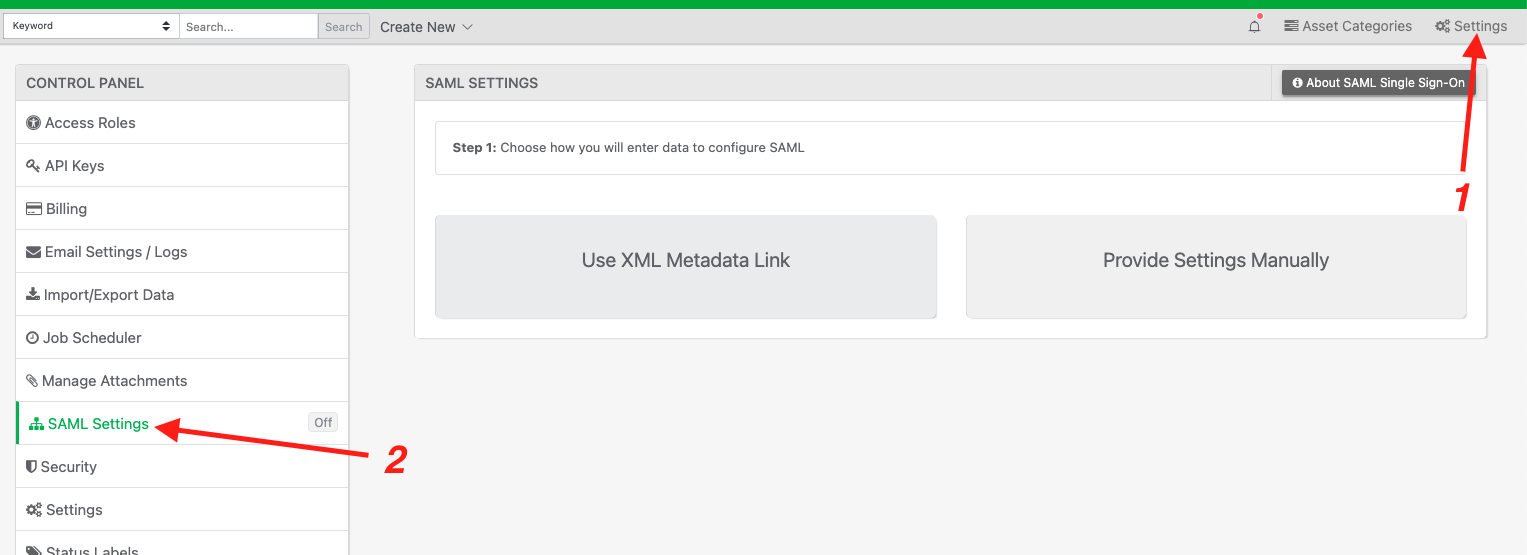
Click “Use XML Metadata Link”.
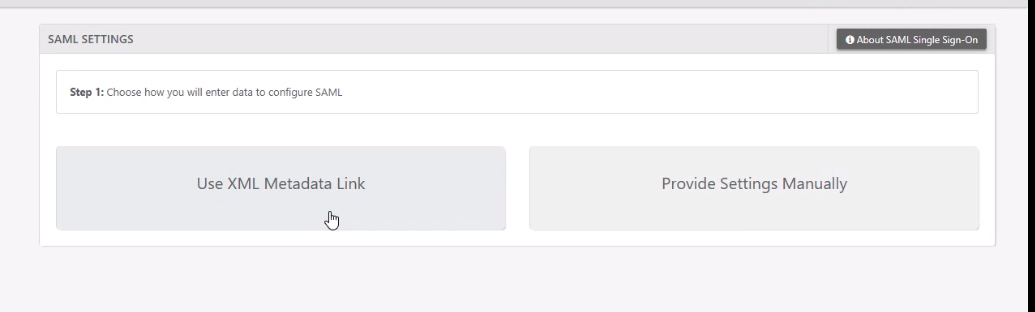
Paste the your metadata URL and click “next”
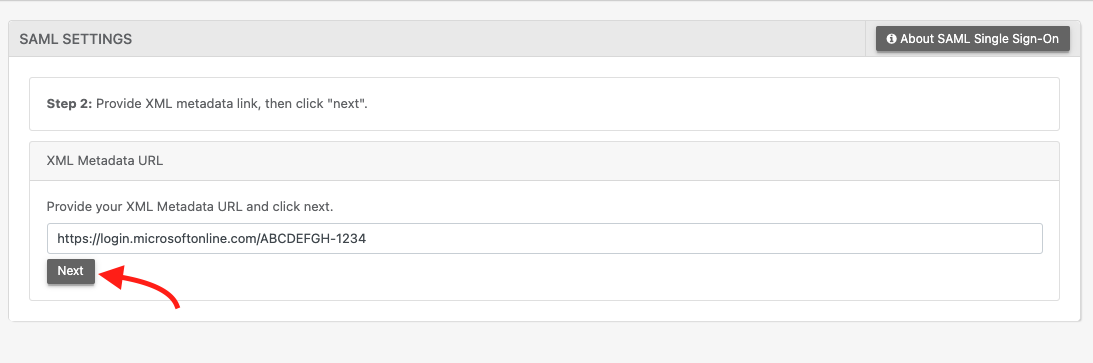
The metadata url will be used to fill in the SAML information in Reftab automatically.
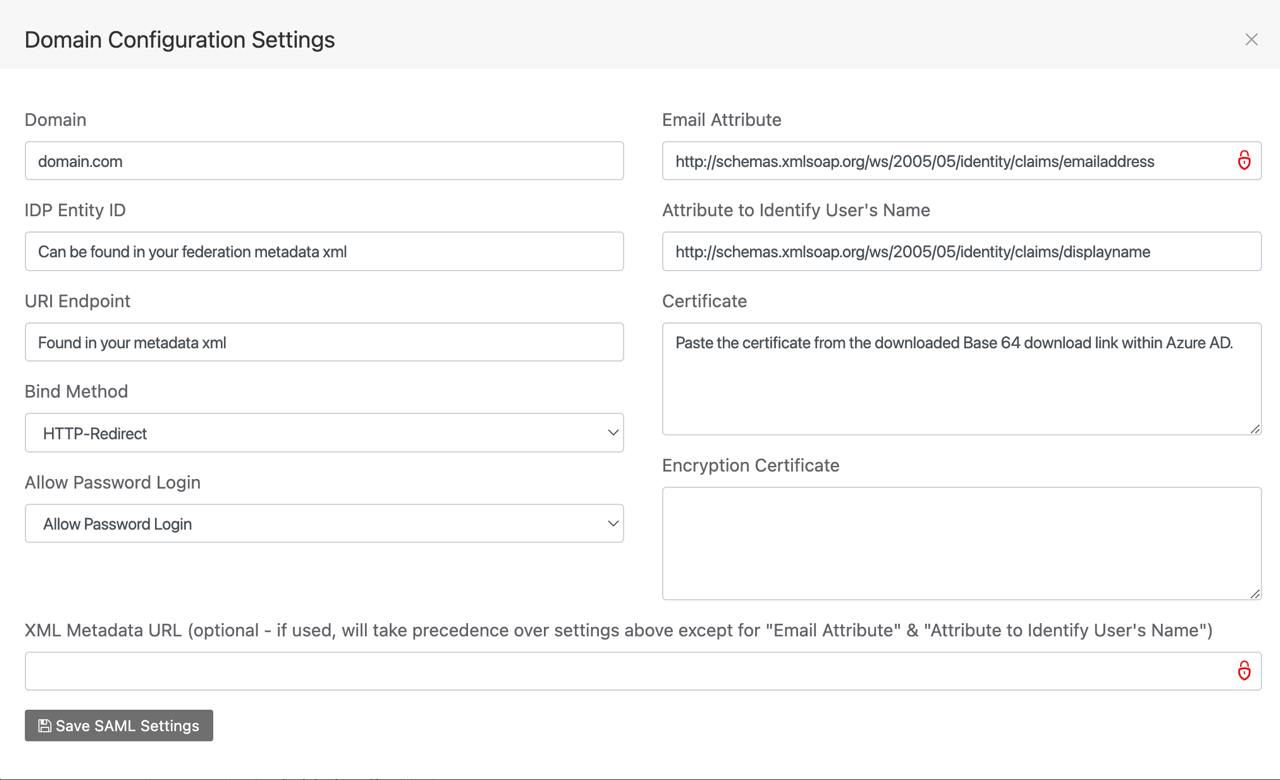
Follow the below if any fields are missing:
Domain: this field should be the part after the ‘@’ symbol in your email. For example: domain.com
IDP Entity ID: This field is your identity provider ID and can be found in your federation metadata xml.
URI Endpoint: This field can be found in your metadata xml.
Bind Method: choose HTTP-Redirect
Email Attribute: This is the attribute that identifies the users email. It can be found in your metadata xml. Usually you can copy this exact string below: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
Attribute to identify users name: This is optional and if used, will save the users name in Reftab. Usually, you can copy this exact string below:
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/displayname
Certificate: Paste the certificate from the downloaded Base 64 download link within Azure AD.
Click, “Save SAML Settings” when done.
Your resulting configuration should look similar to the below image:
Verify Domain Ownership
Next, you will need to verify ownership of your domain before you can begin using SSO with Reftab. This is an important security step. This checks that your domain belongs to you and not anyone else trying to claim it as theirs. Follow this guide to verify your domain: https://www.reftab.com/blog/faq/domain-verification-for-saml/index.html
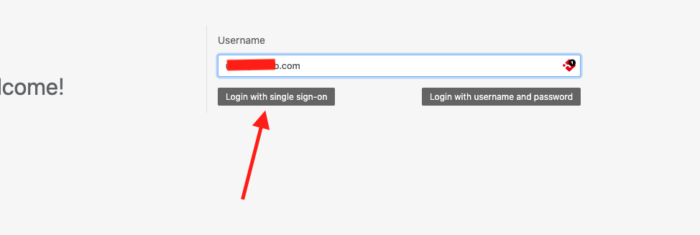
Once domain verification is complete, test logging into Reftab with the user account (or a user within the group) you added to allow access to Reftab in the settings at the start of this guide: https://www.reftab.com/login – type in the users email address and the login screen will detect if your domain is setup and automatically display a button to “Login with single sign-on“
Notes on sign-out process:
After being signed in with SSO. When you log out of Reftab, you may still have an active session with your IDP. You’re still brought to the Reftab logout page, however if you enter your email address (or anyone else’s email address) and click, “login with single sign-on”, you’ll go straight into your account without providing credentials.
This is how single sign-on works when single log-out is not configured. The Azure identity provider keeps the session open. To ensure that you are fully logged out, log out of your Azure account as well.
Reach out to help@reftab.com for further information on single log-out.
Suggested Next Steps
Follow the below next steps to get the most out of your Reftab account and take advantage of further automation.
1. Setup SCIM for Automated User Provisioning with MS Entra
Using SCIM with Reftab automates user management—creating, updating, and deactivating accounts—ensuring accurate asset assignments, improved security, and up-to-date user data across systems.
Click here for how to setup a SCIM integration with Reftab
2. Setup SaaS Discovery to Track Software in Reftab
Enhance your asset management by integrating Reftab with Microsoft Entra for seamless SaaS discovery and utilization tracking. This setup builds on your current infrastructure, automating the management of both hardware and software assets.
Click here for how to setup SaaS Discovery with Reftab
Just-in-time user provisioning:
This is optional and not recommended in most cases. To add users to your Reftab system, it is far more beneficial to setup a SCIM integration.
All users who sign into Reftab must belong to an access role. An access role is something like “Administrator”, “Editor”, “Viewer”, or a custom defined role. Just-in-time provisioning automatically adds users to a role.
Therefore, after you save your SAML settings, you’ll be asked if you would like to setup Just-in-time user provisioning (JIT) roles.
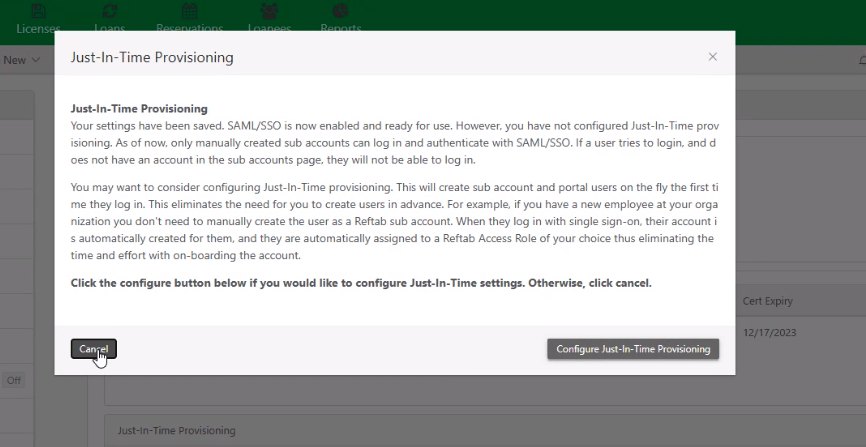
JIT (Just-in-Time) provisioning automatically creates users in Reftab when they first log in, based on SAML token attributes. By setting up JIT rules (e.g., department-based), users are assigned to the correct Reftab role—like Admin for IT or Portal User for Marketing—saving time and ensuring proper access. Users who don’t match a rule won’t be able to log in.
To setup additional role claims for just-in-time provisioning, follow this document from MS: https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-enterprise-app-role-management
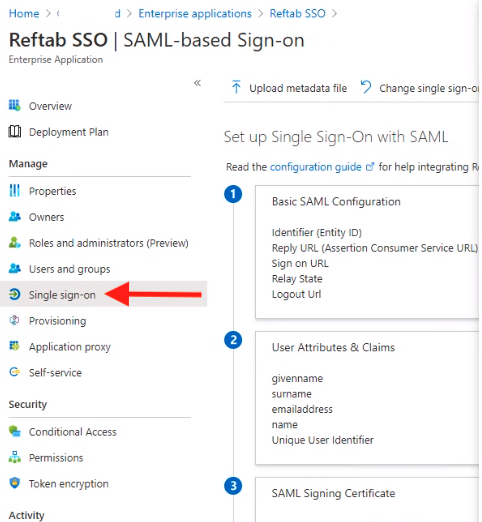
Within your Azure AD account click, “Reftab”

Then, select “Single Sign-on” and for the section “User Attributes & Claims” click “edit” you can manage the claims that are sent on your SAML token. You can add / remove cliams which can be used on the Just-in-time settings.
Reach out to help@reftab.com for any questions. We are happy to help.